An Ids May Use Which of the Following Techniques
Network and analyzing them for signs of possible incidents which are violations or imminent. It can be used to evade some of the rules in the firewalls or IDS.
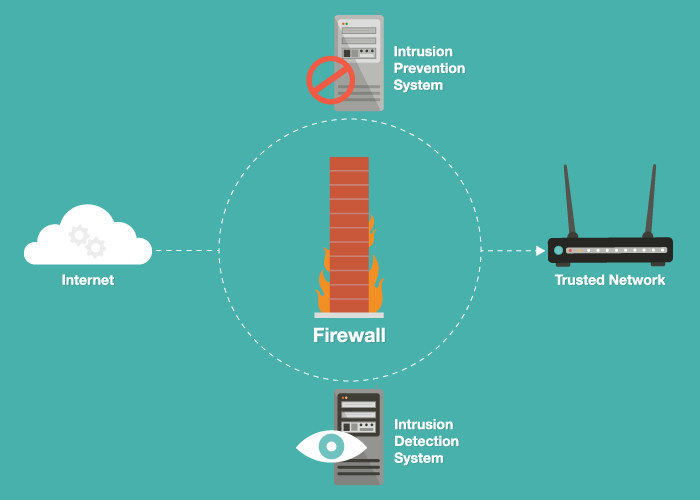
What Type Of Intrusion Detection And Prevention System Do I Need
Can inspect code of network drivers 24.
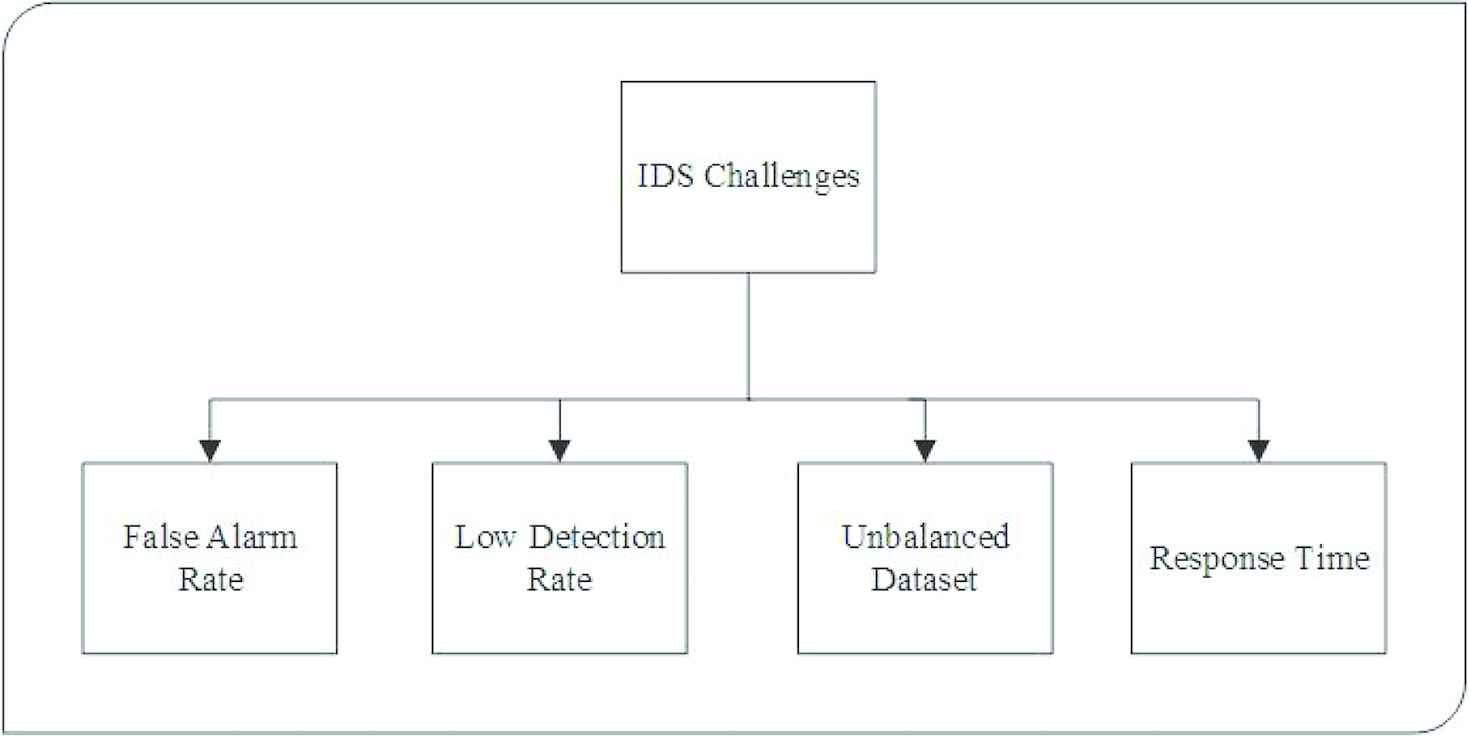
. Signature Recognition Anomaly Detection Protocol Anomaly Detection Obfuscating. This functionality could also be built into remote. Techniques to Detect Fraud Analytics These days Business data is being managed and stored by IT systems in an organization.
While anomaly detection and reporting are the primary functions of an IDS some intrusion detection systems are capable of taking actions when malicious activity or anomalous traffic is detected including blocking traffic sent from. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management system. Following through on their primary objective often requires exploring the network to find their target and subsequently gaining access to it.
Analyze and monitor traffic for indicators of compromise that may indicate an intrusion or data theft. Question 2 2 out of 2 points One way to harden a system is to make sure user account names are not obvious and default accounts are disabled. Paranoid Waits 5 minutes between sending each probes not detected by IDSIPS T1.
Fragmentation obfuscation and encryption are all evasive techniques used by attackers to dodge IDS detection. Reaching their objective often involves pivoting through multiple systems and accounts to gain. Therefore organizations rely more on IT systems to support business processes.
Methods for performing this technique could include use of a Command and Scripting Interpreter to search for and copy information fitting set criteria such as file type location or name at specific time intervals. IDS systems compare the current network activity to a known threat database to detect several kinds of behaviors like security policy violations malware and port scanners. Intrusion Detection and Prevention Systems.
Which of the following IDS detection technique detects the intrusion based on the fixed behavioral characteristics of the users and components in a computer system. Once established within a system or network an adversary may use automated techniques for collecting internal data. Lateral Movement consists of techniques that adversaries use to enter and control remote systems on a network.
A Cross-site request forgery attack B Cross-site script attack C Session replay attacks D Session fixation. An intrustion detection system IDS is a software application or hardware appliance that monitors traffic moving on networks and through systems to search for suspicious activity and known. Analyze and monitor network traffic for signs that indicate attackers are using a known cyberthreat to infiltrate or steal data from your network.
12 password-cracking techniques used by hackers. In addition to restricting network activity companies are increasingly monitoring traffic with intrusion detection systems IDS. IDS require humans or another system to look at the results and to determine how to respond making them better as.
A SIEM system combines outputs from multiple sources and uses alarm. Network Node Intrusion Detection System. A writer may use all of the following techniques to lead the reader to a flashback EXCEPT.
T5Insane easily detectable Usage. Intrusion detection is the process of monitoring the events occurring in a computer system or. Which of the following intrusion detection technique involves first creating models of possible intrusions and then comparing these models with incoming events to make a detection decision.
Intrusion Detection Systems IDS. IDS system may favor freshest fragment overwriting older data - fragment conflict Reassembled packet at end-system can be different than what IDS sees thus effectively evading IDS Difficult to exploit but not impossible Attacker must know the inconsistencies of fragment handling on IDS or end-system eg. Question 1 2 out of 2 points Which of the following IDS techniques seeks to prevent intrusions before they occur.
A detailed explanation C. IDS compares current network activity against known threats security policy violations and open port scanning. Phishing is among the most common password-stealing techniques currently in use today and is often used for other types.
Denial-of-service and access attacks are forms of attacks performed by hackers but are not directly used to compromise IDSs. At the most basic level Network Intrusion Detection Systems and Network Node Intrusion Detection Systems look at network traffic while Host Intrusion Detection Systems look at actions and files on the host devices. Launch an FTP bounce scan idle scan fragmentation attack or try to tunnel through one of your own proxies.
At the same time the target machine experiences the malicious attack. An intrusion detection system IDS is a system that monitors network traffic for suspicious activity and alerts when such activity is discovered. Which of the following techniques is also called a one-click attack or session riding and is used by an attacker to exploit a victims active session with a trusted site to perform malicious activities.
Threats of violation of computer security policies acceptable use policies or standard security. Sneaky waits 15 seconds T2Polite. Intrusion detection systems IDS.
Place yourself in the mind-set of an attacker and deploy techniques from this section against your networks. There are various timing options included in the nmap to send successive packets. Signature recognition Anomaly detection Protocol anomaly detection All of the above.
The IDS sensor using a signature matches the malicious traffic to the signature. The switch sends copies of all packets to the IDS sensor configured in promiscuous mode which is explained later in this section to analyze the packets. Host Intrusion Detection System.
An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations. Answers B D and E are correct. Because of such IT systems the level of human interaction has been reduced to a greater extent which in turn becomes the main reason for fraud to take place in an.
A clue about future events A clue about future events may not be used to lead the reader to a flashback.
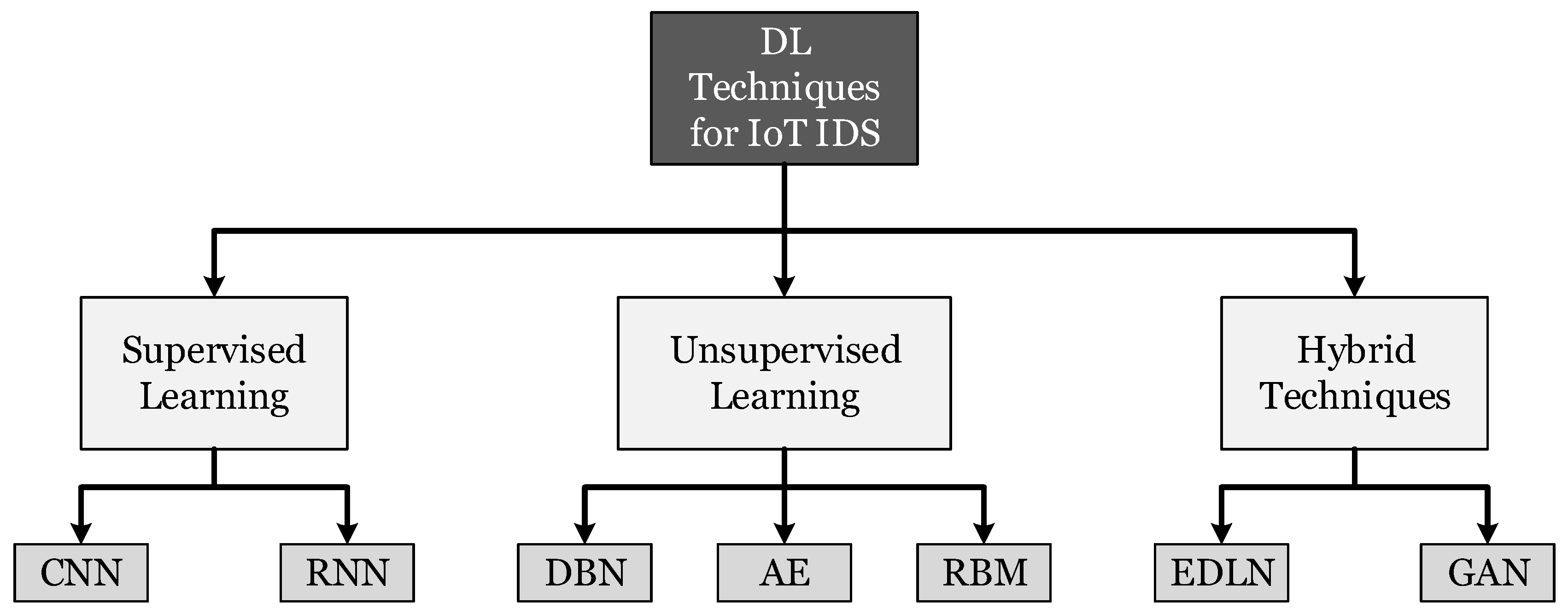
Electronics Free Full Text A Review Of Intrusion Detection Systems Using Machine And Deep Learning In Internet Of Things Challenges Solutions And Future Directions Html
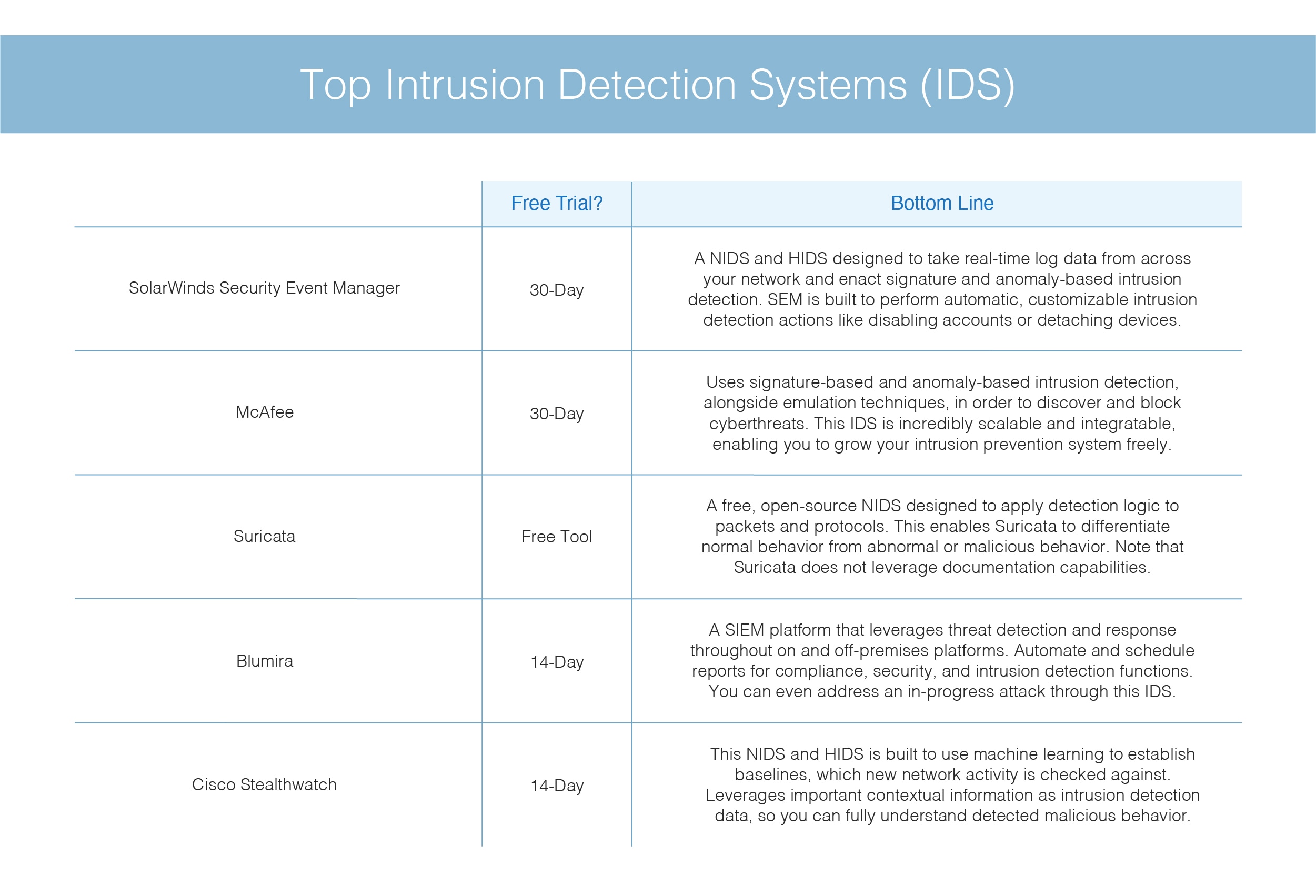
What Is An Intrusion Detection System Ids Definition And Software Solarwinds
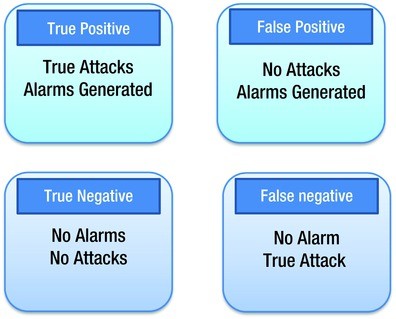
Intrusion Detection And Prevention Systems Springerlink
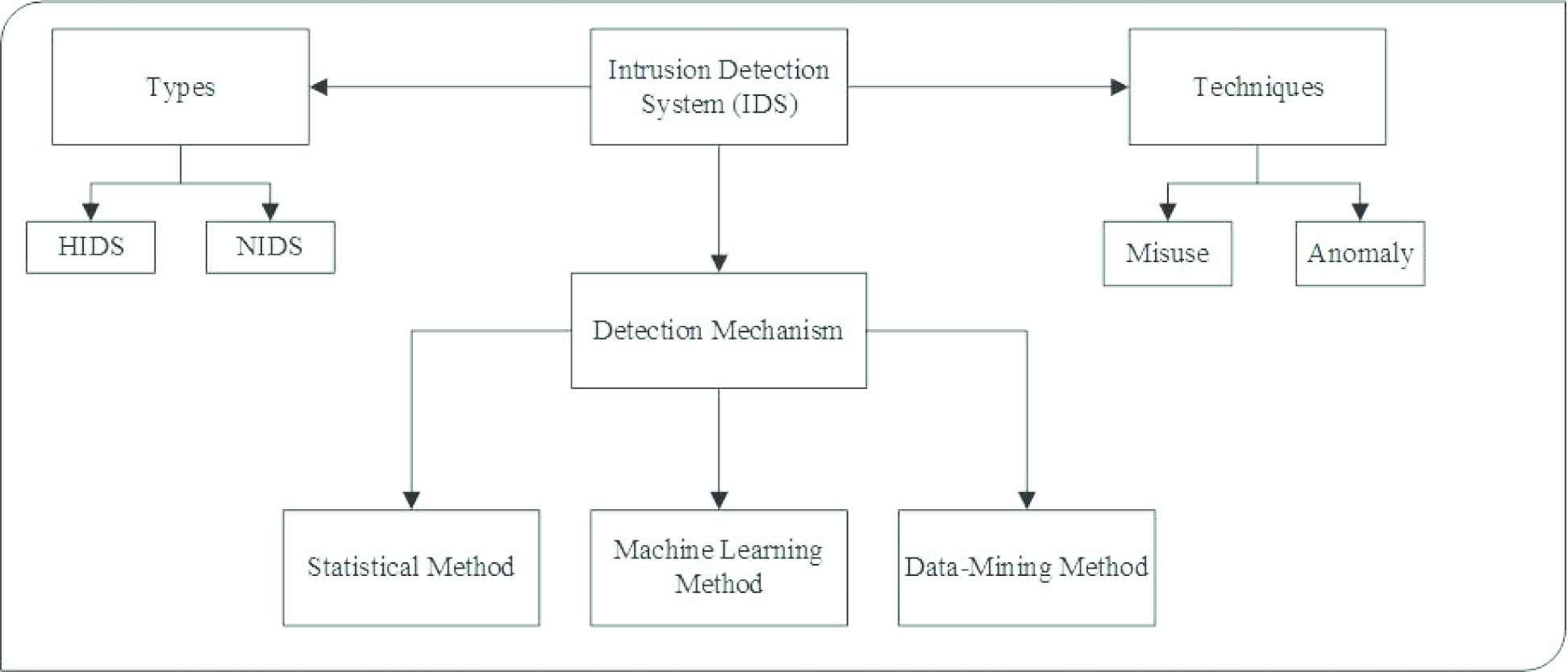
Intrusion Detection Systems Issues Challenges And Needs Atlantis Press
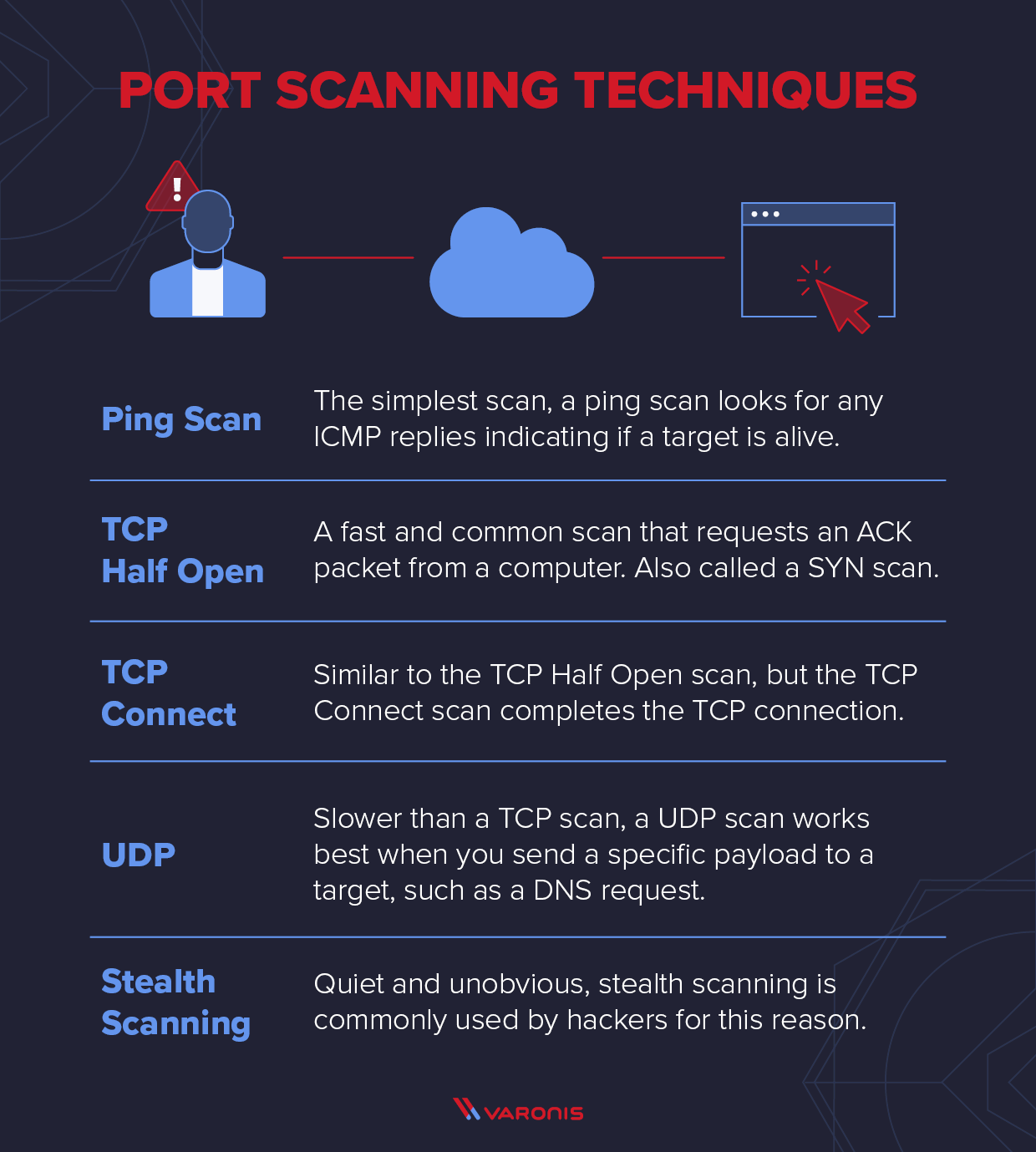
What Is A Port Scanner And How Does It Work
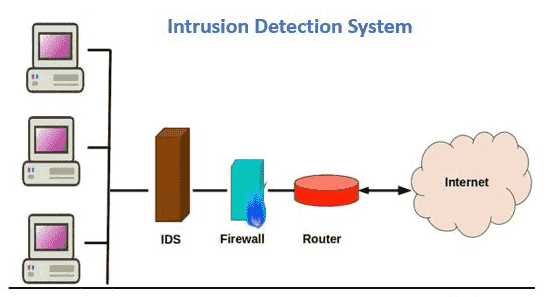
What Is An Intrusion Detection System Ids Ids Security 2022
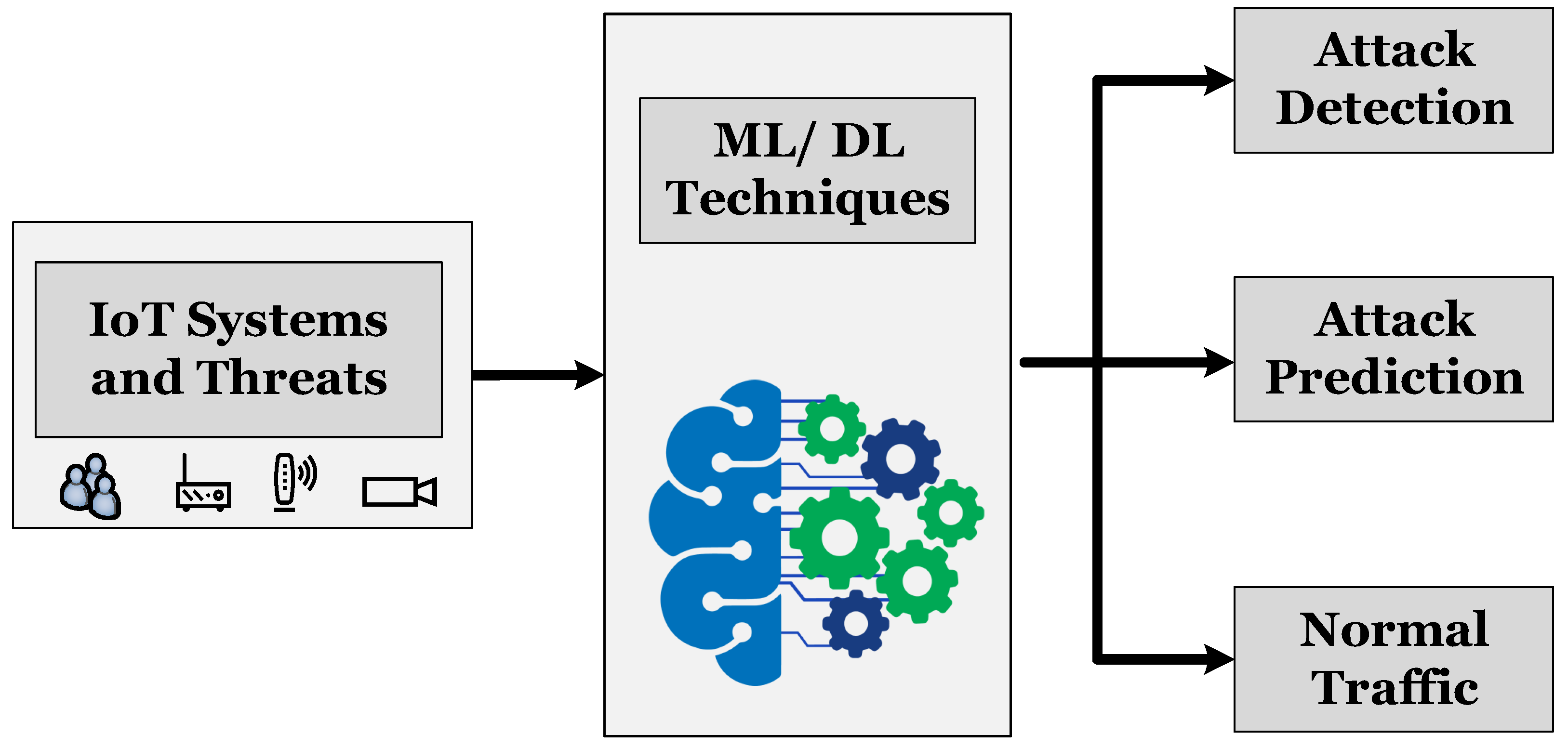
Electronics Free Full Text A Review Of Intrusion Detection Systems Using Machine And Deep Learning In Internet Of Things Challenges Solutions And Future Directions Html
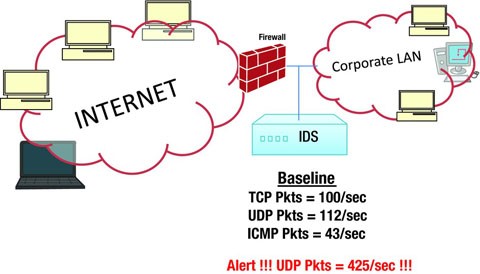
Intrusion Detection And Prevention Systems Springerlink
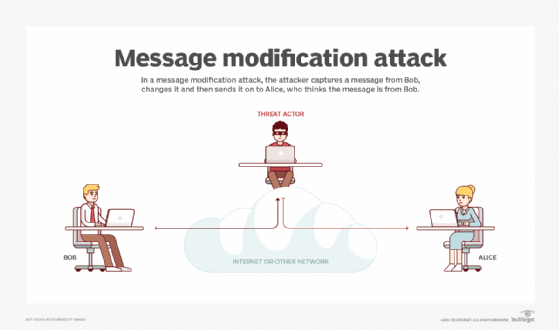
What Is An Active Attack Definition From Whatis Com

Intrusion Detection And Prevention An Overview Sciencedirect Topics

Intrusion Detection Systems Issues Challenges And Needs Atlantis Press

Network Based Intrusion Detection System An Overview Sciencedirect Topics
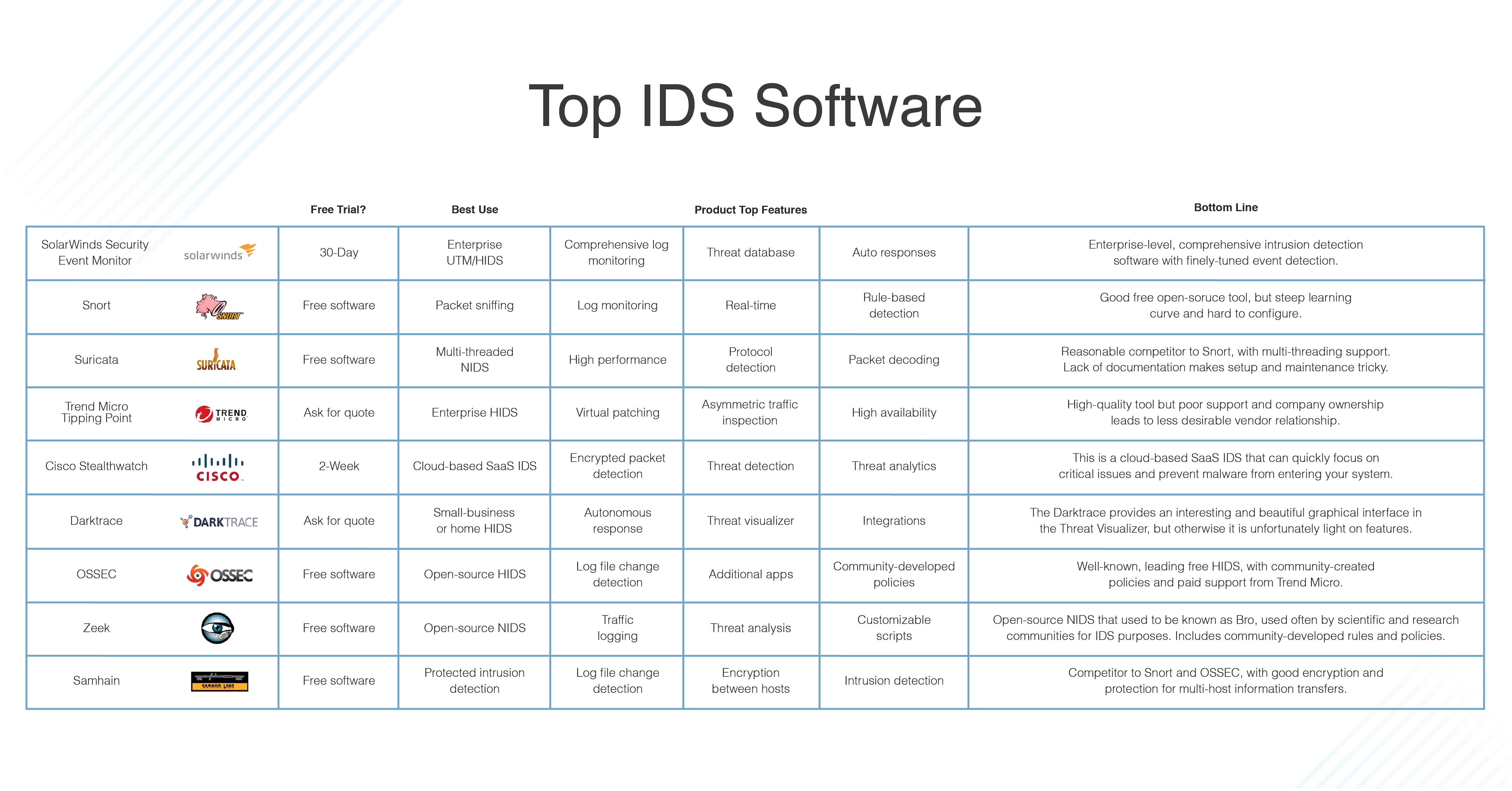
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff

Network Based Intrusion Detection System An Overview Sciencedirect Topics
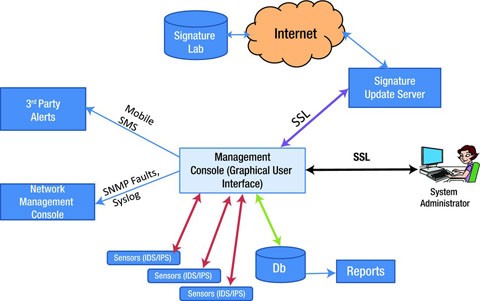
Intrusion Detection And Prevention Systems Springerlink
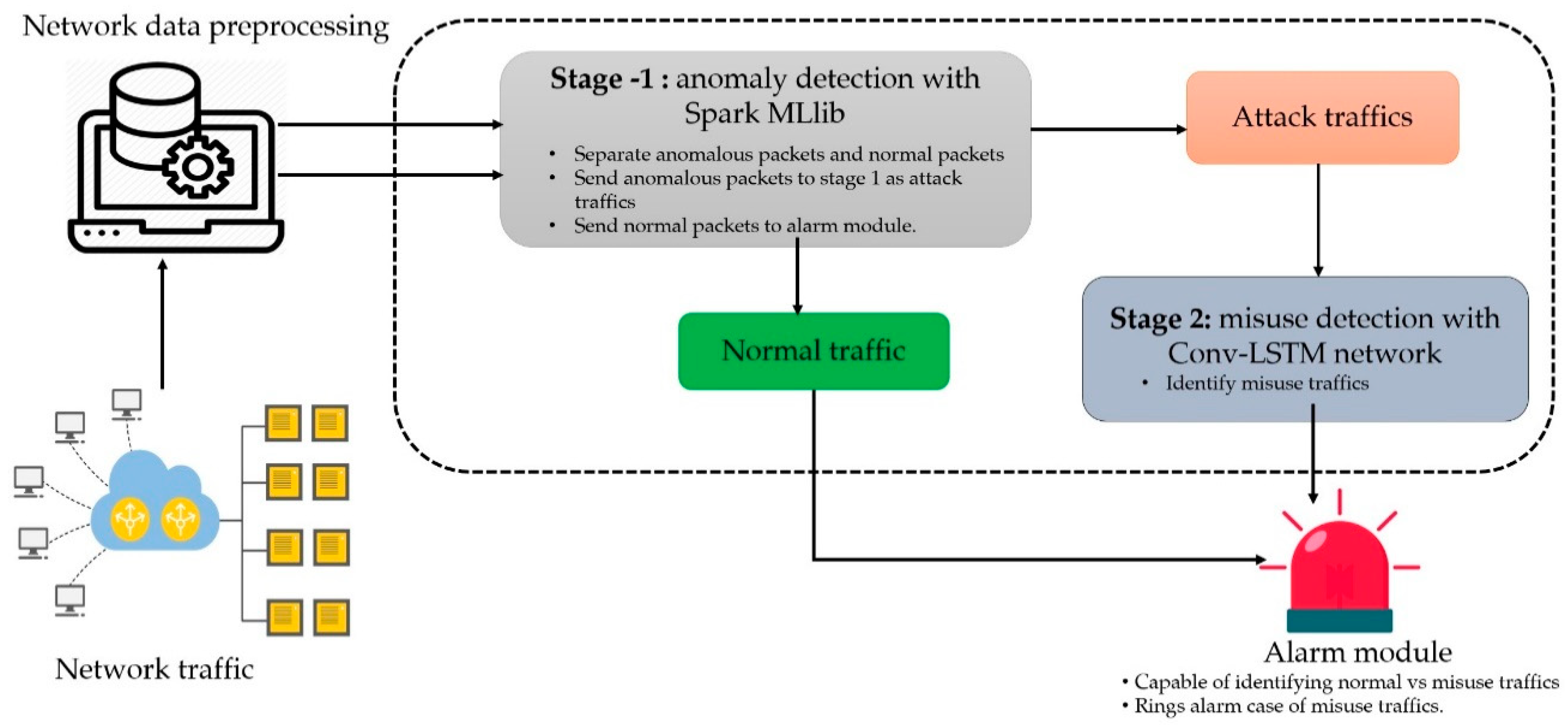
Symmetry Free Full Text A Scalable And Hybrid Intrusion Detection System Based On The Convolutional Lstm Network Html
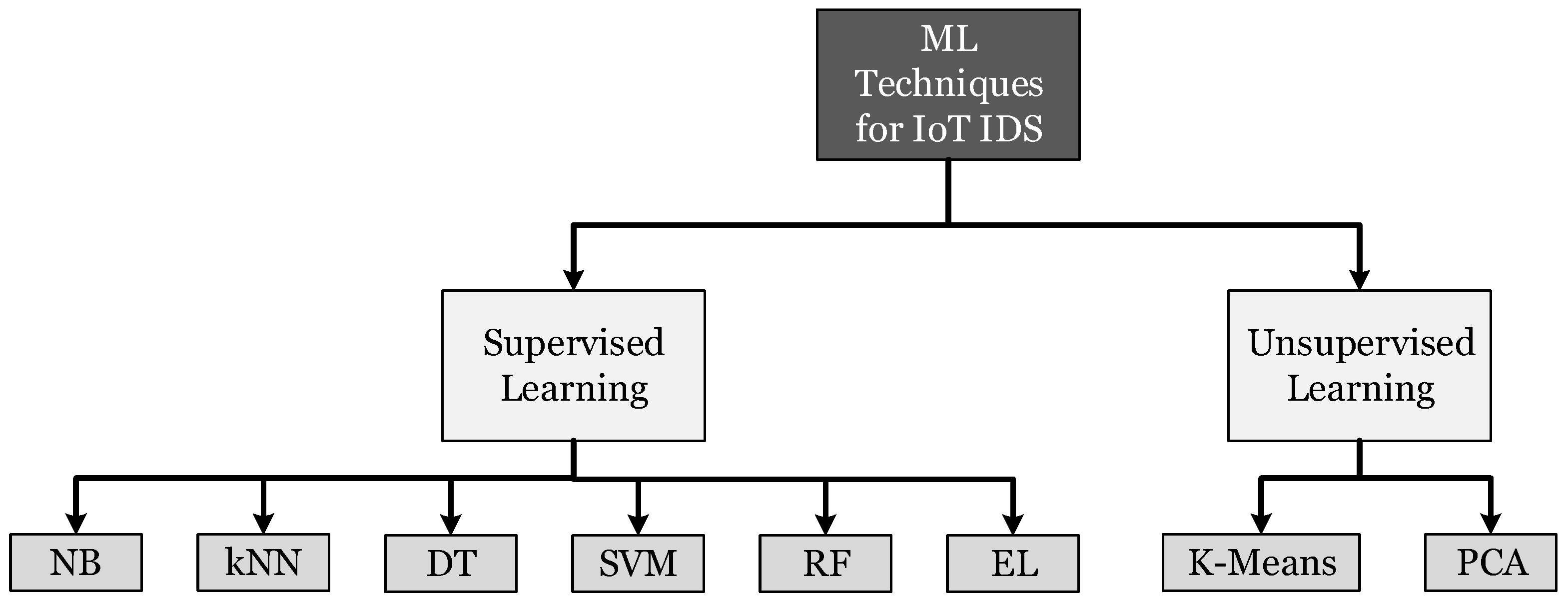
Electronics Free Full Text A Review Of Intrusion Detection Systems Using Machine And Deep Learning In Internet Of Things Challenges Solutions And Future Directions Html


Comments
Post a Comment